
AXK MAINNET
2.4.0 (GENESIS)
UPTIME: 99.99%
PEER LATENCY: 12ms
FINALITY TTF: 1.2s
TVL ROUTED: $45,210,900 USD



AXK MAINNET
2.4.0 (GENESIS)
UPTIME: 99.99%
PEER LATENCY: 12ms
FINALITY TTF: 1.2s
TVL ROUTED: $45,210,900 USD

Autonomous exchange kernel
Autonomous exchange kernel
AXK ensures capital moves only when real-world state is cryptographically verified.
AXK ensures capital moves only when real-world state is cryptographically verified.
Read white paper
Backed by
Backed by
Supporting UN Sustainable Development Goals
Supporting UN Sustainable Development Goals
Supporting UN Sustainable Development Goals
AXK supports SDGs 8, 9, 13, 16, and 17 by securing supply chains, building trusted digital infrastructure, enabling verifiable climate data, strengthening institutional transparency, and enabling cross-sector collaboration.
AXK supports SDGs 8, 9, 13, 16, and 17 by securing supply chains, building trusted digital infrastructure, enabling verifiable climate data, strengthening institutional transparency, and enabling cross-sector collaboration.
AXK supports SDGs 8, 9, 13, 16, and 17 by securing supply chains, building trusted digital infrastructure, enabling verifiable climate data, strengthening institutional transparency, and enabling cross-sector collaboration.















THE CORE PROBLEM
THE CORE PROBLEM
THE CORE PROBLEM
Why the Global Economy Breaks at Scale
Why the Global Economy Breaks at Scale
Why the Global Economy Breaks at Scale
Physical Reality
Physical Reality
Physical reality is continuous and adversarial, shaped by sensor-dependent signals and human influence that constantly introduce uncertainty and variability.
Physical reality is continuous and adversarial, shaped by sensor-dependent signals and human influence that constantly introduce uncertainty and variability.
Physical reality is continuous and adversarial, shaped by sensor-dependent signals and human influence that constantly introduce uncertainty and variability.
Financial Systems
Financial Systems
Financial systems are discrete and ledger-based, while the real world is not. Legacy approaches rely on documents, intermediaries, and reconciliation, adding friction and delay.
Financial systems are discrete and ledger-based, while the real world is not. Legacy approaches rely on documents, intermediaries, and reconciliation, adding friction and delay.
Financial systems are discrete and ledger-based, while the real world is not. Legacy approaches rely on documents, intermediaries, and reconciliation, adding friction and delay.
AXK is a horizontal grid, not a layered stack.
AXK is a horizontal grid, not a layered stack.
AXK unifies state observation, contextual authorization, and capital execution into a single deterministic system that turns real-world events into financial finality.
AXK unifies state observation, contextual authorization, and capital execution into a single deterministic system that turns real-world events into financial finality.
All components consume the same Trust Layer.
All components consume the same Trust Layer.

Plane A — Physical Mesh: Signs real-world events into verifiable state.
Plane A — Physical Mesh: Signs real-world events into verifiable state.

Plane B — Identity Fabric: Resolves authorization, ownership, and compliance.
Plane B — Identity Fabric: Resolves authorization, ownership, and compliance.

Plane C — Liquidity Core: Executes final settlement on verified state.
Plane C — Liquidity Core: Executes final settlement on verified state.


A Cryptographic State Transition Model for the Real World
A Cryptographic State Transition Model for the Real World
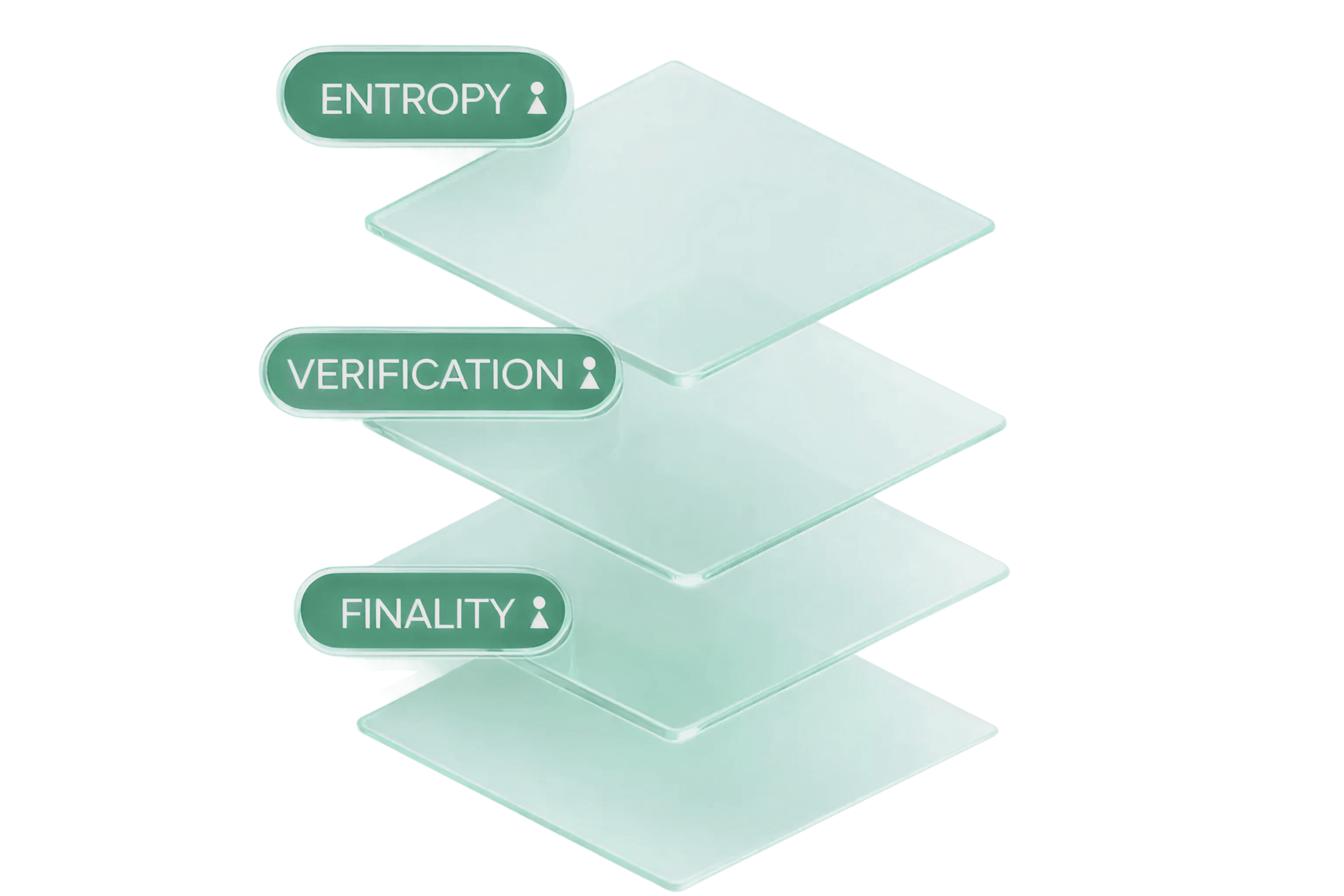
PHASE I — INGEST (ENTROPY)
AXK ingests untrusted observations from the edge of the network across sensors, machines, human operators, and third party oracles, where events exist only as signed claims and truth has not yet been established.
PHASE II — CONSENSUS (TRUST)
Only when a physical event is cryptographically proven as real and the actors and assets involved are contextually verified for identity, jurisdiction, compliance, solvency, and ownership can the event advance to final state.

PHASE III — EXECUTE (FINALITY)
Upon verification, the Kernel emits a STATE VERIFIED event that atomically triggers irreversible settlement, releasing capital within the same finalized block and making the outcome globally observable, with no possibility of a verified-but-unsettled state.
PHASE I — INGEST (ENTROPY)
AXK ingests untrusted observations from the edge of the network across sensors, machines, human operators, and third party oracles, where events exist only as signed claims and truth has not yet been established.

PHASE II — CONSENSUS (TRUST)
Only when a physical event is cryptographically proven as real and the actors and assets involved are contextually verified for identity, jurisdiction, compliance, solvency, and ownership can the event advance to final state.

PHASE III — EXECUTE (FINALITY)
Upon verification, the Kernel emits a STATE VERIFIED event that atomically triggers irreversible settlement, releasing capital within the same finalized block and making the outcome globally observable, with no possibility of a verified-but-unsettled state.

PHASE I — INGEST (ENTROPY)
AXK ingests untrusted observations from the edge of the network across sensors, machines, human operators, and third party oracles, where events exist only as signed claims and truth has not yet been established.

PHASE II — CONSENSUS (TRUST)
Only when a physical event is cryptographically proven as real and the actors and assets involved are contextually verified for identity, jurisdiction, compliance, solvency, and ownership can the event advance to final state.

PHASE III — EXECUTE (FINALITY)
Upon verification, the Kernel emits a STATE VERIFIED event that atomically triggers irreversible settlement, releasing capital within the same finalized block and making the outcome globally observable, with no possibility of a verified-but-unsettled state.

DEVELOPER INTERFACE
DEVELOPER INTERFACE




NODE TYPE SPECIFICATION
NODE TYPE SPECIFICATION
AXK is composed of distinct node types, each with a clear role introducing reality, preserving custody, executing capital, deriving intelligence, and providing oversight—working together to turn verified real-world state into financial finality.
AXK is composed of distinct node types, each with a clear role introducing reality, preserving custody, executing capital, deriving intelligence, and providing oversight—working together to turn verified real-world state into financial finality.

Originator Nodes; Source of Reality
Originator Nodes; Source of Reality
Originator Nodes introduce new physical assets into AXK by cryptographically proving origin and extraction, unlocking liquidity the moment reality is verified.
Originator Nodes introduce new physical assets into AXK by cryptographically proving origin and extraction, unlocking liquidity the moment reality is verified.
Vector Nodes; Continuous Custody
Vector Nodes; Continuous Custody
Vector Nodes preserve uninterrupted custody as assets move through the real economy, cryptographically proving transit and enabling instant payment with zero receivables.
Vector Nodes preserve uninterrupted custody as assets move through the real economy, cryptographically proving transit and enabling instant payment with zero receivables.

Liquidity Nodes; Capital With Finality
Liquidity Nodes; Capital With Finality
Liquidity Nodes transform verified real-world state into atomic settlement, deploying conditional capital only when truth is finalized, maximizing yield while minimizing fraud.
Liquidity Nodes transform verified real-world state into atomic settlement, deploying conditional capital only when truth is finalized, maximizing yield while minimizing fraud.
Logic Nodes; Intelligence on Truth
Logic Nodes; Intelligence on Truth
Logic Nodes derive automated decisions from verified state, pricing risk, triggering parametric actions, and emitting cryptographic proofs at scale, without manual intervention.
Logic Nodes derive automated decisions from verified state, pricing risk, triggering parametric actions, and emitting cryptographic proofs at scale, without manual intervention.
Observer Nodes; Oversight Without Control
Observer Nodes; Oversight Without Control
Observer Nodes provide real-time, read-only visibility into state and flows, enabling compliance, policy enforcement, and sovereignty without direct execution authority.
Observer Nodes provide real-time, read-only visibility into state and flows, enabling compliance, policy enforcement, and sovereignty without direct execution authority.
Participate in the AXK network
AXK has no customers; it is composed of members who operate nodes in a permissionless network, where responsibilities are defined by role and enforced directly by the protocol.

Participate in the AXK network
AXK has no customers; it is composed of members who operate nodes in a permissionless network, where responsibilities are defined by role and enforced directly by the protocol.

Participate in the AXK network
AXK has no customers; it is composed of members who operate nodes in a permissionless network, where responsibilities are defined by role and enforced directly by the protocol.

Participate in the AXK network
AXK has no customers; it is composed of members who operate nodes in a permissionless network, where responsibilities are defined by role and enforced directly by the protocol.
Join our newsletter
Infrastructure that verifies every transaction.
About
Docs
Resources
Code Samples
Dev Tools
AXK Learning Portal
AXK Brand Kit
Ledger Explorer
Contribute Code
Contribute Documentation
Community
Community
Events
Ambassadors
Developer Funding
AXK Jobs
AXK Ledger Community Blog
AXK Grants
GitHub
Report a Scam







